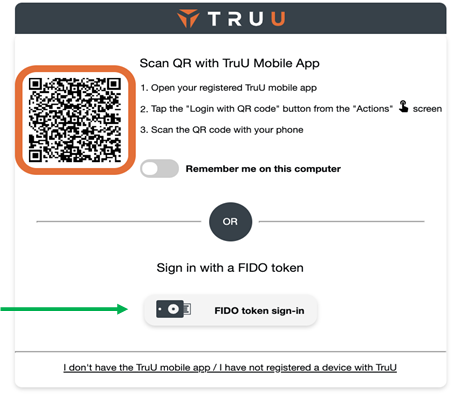
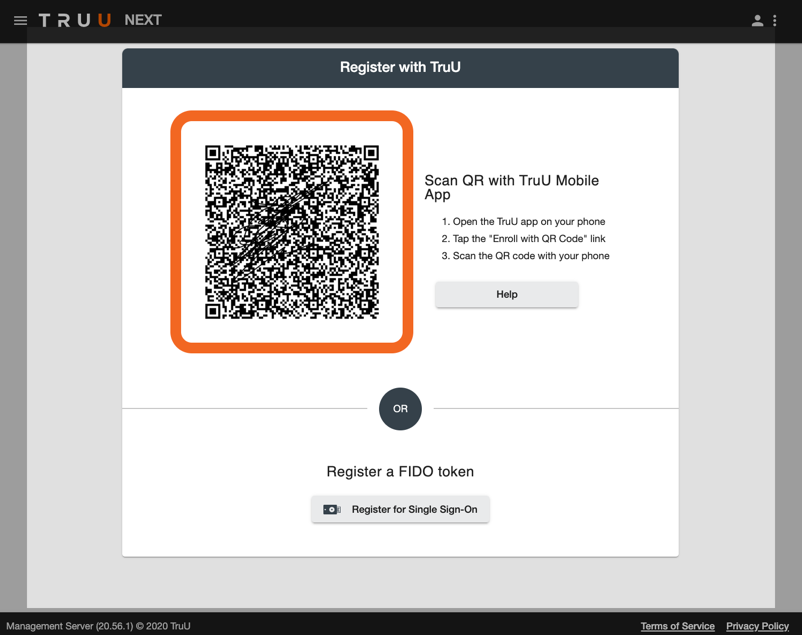
In speaking with customers and prospective customers, we understand that not all employees carry a smartphone, or may not wish to use their personal phone for access. To address this class of users, and to provide alternative login methods for users with smartphones, we are very excited to announce that we have added support for using FIDO hardware keys for passwordless access through TruU.
Enterprise IAM Administrators Enable Yubikeys First
Admins can now enable their users to enroll FIDO2-compatible hardware keys as a way to identify themselves. Currently, FIDO hardware key support is limited to application access but is available for all of our SSO integrations. To see for yourself how this works, you will need to do the following:
- Go to ‘Settings’ > ‘Security’ and check the box to ‘Include Option to Enroll a FIDO Token’ this will allow users to enroll a FIDO key through the enrollment interface.
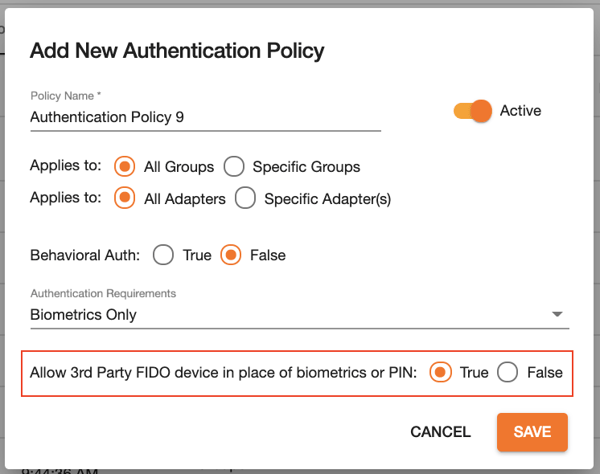
2. Go to ‘Policies’ > ‘Authentication’ and set the ‘Allow 3rd Party FIDO device in place of biometrics or PIN’ policy to ‘True’.
All apps federated with a single IdP will authenticate to the same origin (the IdP itself). We have made it very simple for this setup by automatically adding the origin for all existing SSO integrations. Management of those origins is available through the new ‘Settings’ > ‘FIDO’ > ‘Relying Party Origins’ menu, and individual origins can be modified by clicking on a specific SSO adapter from the ‘Integrations’ menu.
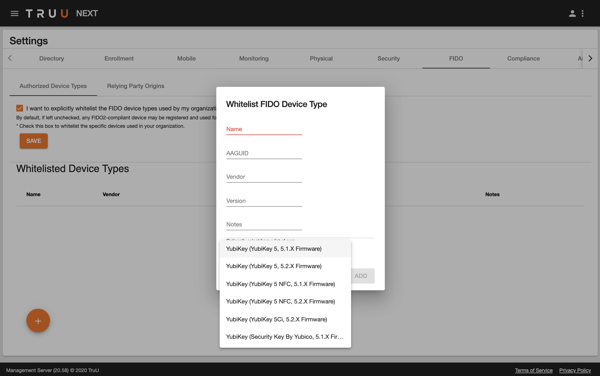
If your company has standardized on Yubikeys and wants to limit the enrollment of FIDO2-compatible hardware to devices from Yubico, you can do this by whitelisting the devices you wish to allow. This can be enabled by going to the ‘Settings’ > ‘FIDO’ > ‘Authorized Device Types’ menu, and choosing the option to whitelist FIDO device types.
End User Workflow for Enabling Yubikeys
With this in place, TruU end users can now authenticate using a FIDO2-compatible hardware key in lieu of a mobile device. When logging into an application that is enabled for TruU login, the user can now click a button to log in with a FIDO token which will start the FIDO login flow.
![]()